Panorama Best Practices Assessment.

The Palo Alto Networks Best Practice Assessment (BPA) tool can be used to check the security posture of both Panorama and firewall deployments, by comparing the current configuration of the devices against the Palo Alto Network best practices. The BPA can be re-run at any time normally every 90 days. Included in the report is a spreadsheet where it shows details of passed & failed BPA configurations. I like to use this after an initial Panorama/Firewall deployment to get a baseline and then start working through the failed elements of the report and essentially tick them off one by one, starting with the low hanging fruit.
In this article, I'll run through a Panorama BPA and tackle some failed BPA results.
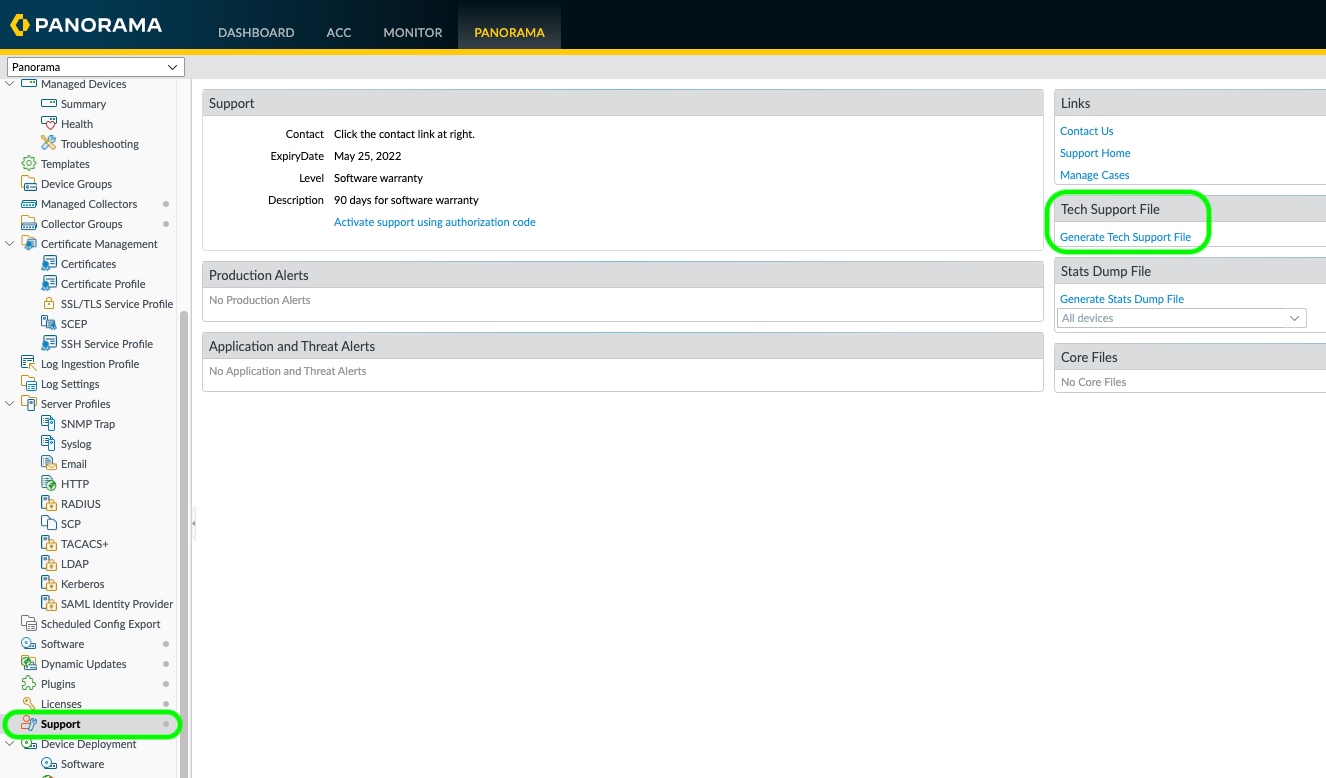
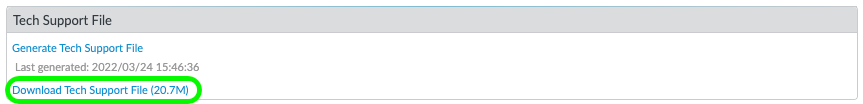
To start with we need to generate a Tech Support file within the Panorama WebUI. Click on the Panorama tab, and on the left, we need to find the support section, on the right-hand side there is a "Generate Support File" link, click that and wait for the file to generate and download to your client machine.
Now we need to browse to the Palo Alto Networks Customer Support Portal (CSP)
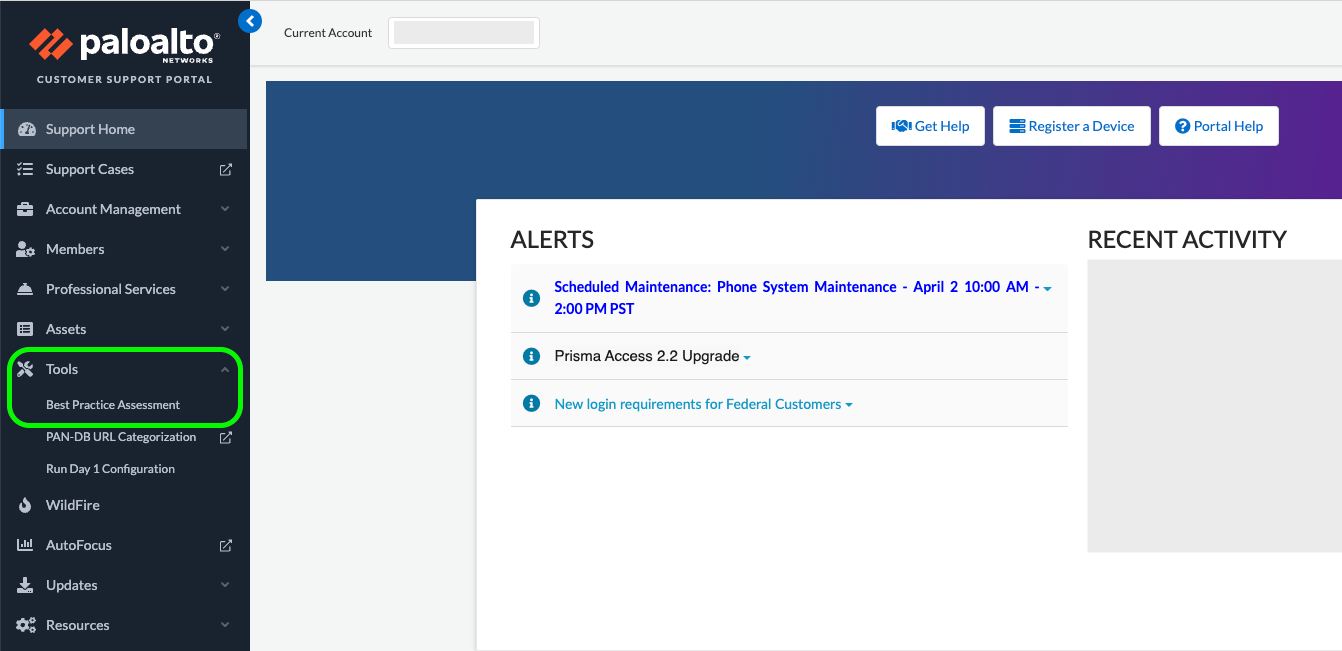
Expand the Tools heading and select "Best Practices Assessment"
Once the Window opens click on the "Generate New BPA"
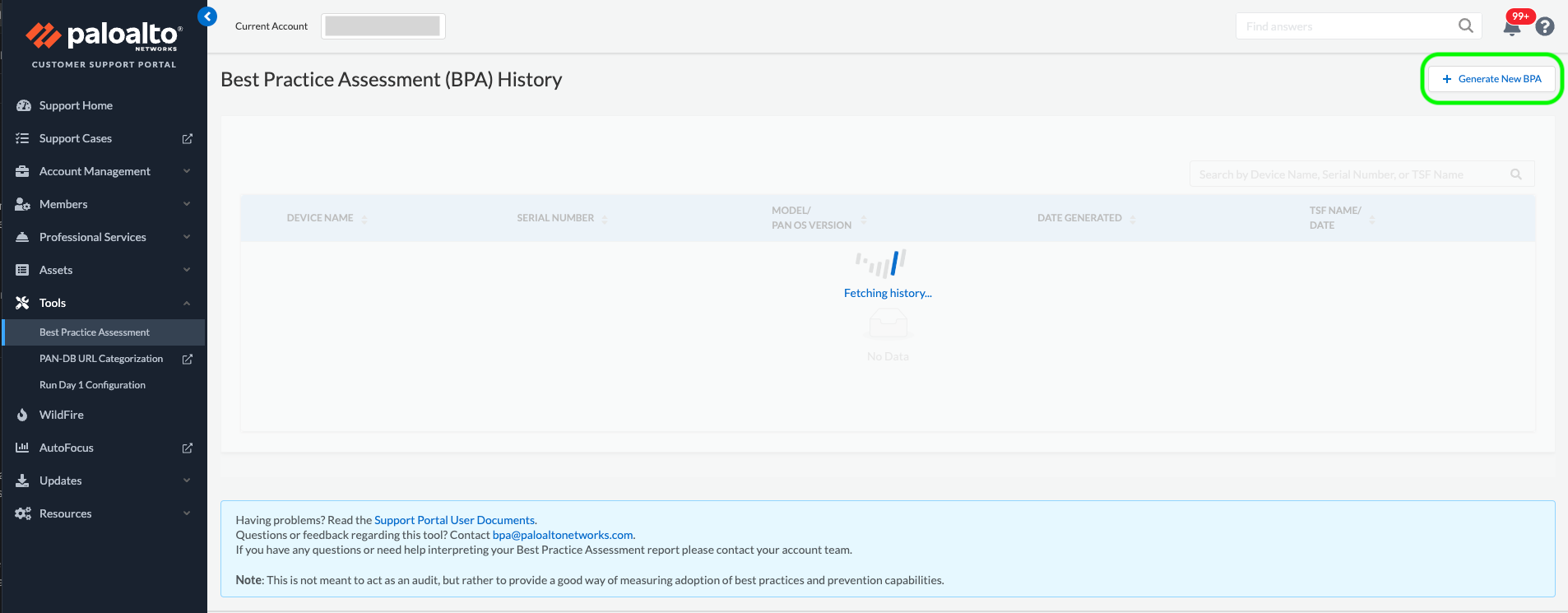
This is where you can drag or browse to the Tech Support file that was generated earlier.
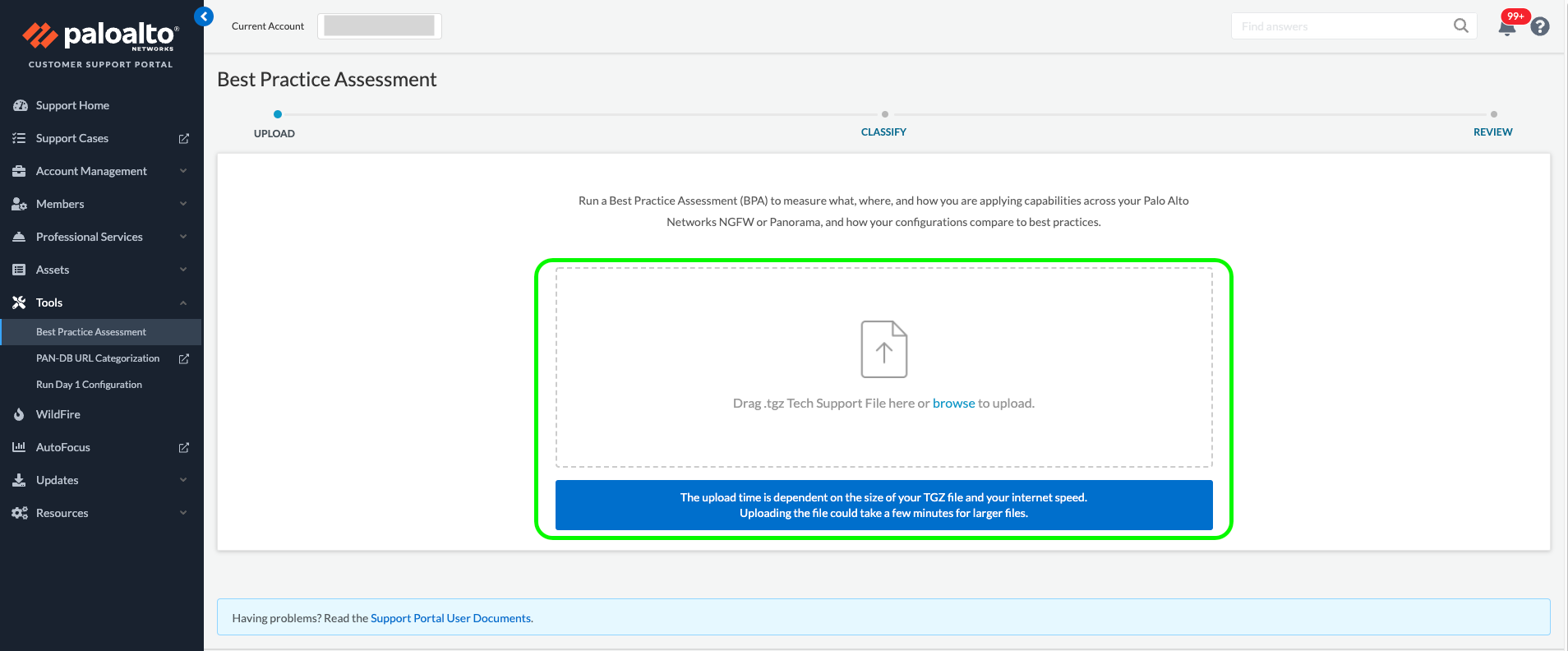
Once the Tech Support file has been uploaded you will be presented with the "Architecture Classification" page, this can be skipped as it relates to firewall Zone mappings and not Panorama.
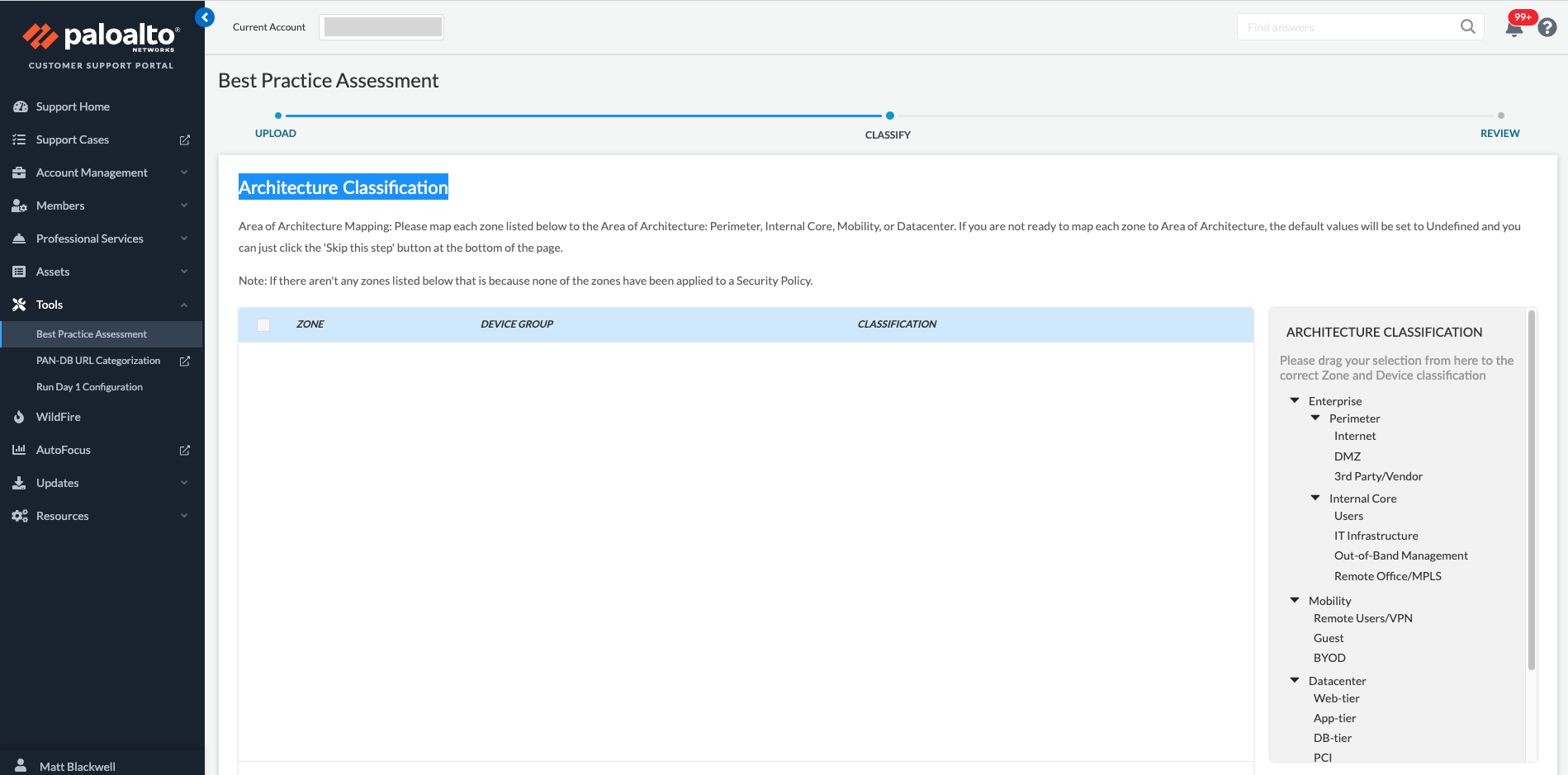
The default Industry is High Technology, I'm just going to leave it at that, however, if you want to compare your BPA against a particular industry, take a look through the list and choose the right one for you. When you are ready hit the "Generate & Download Report" button.
Keep an eye out for the pop-up boxes in the left-hand corner. You should get a prompt to save the zip file to a location of your choosing.
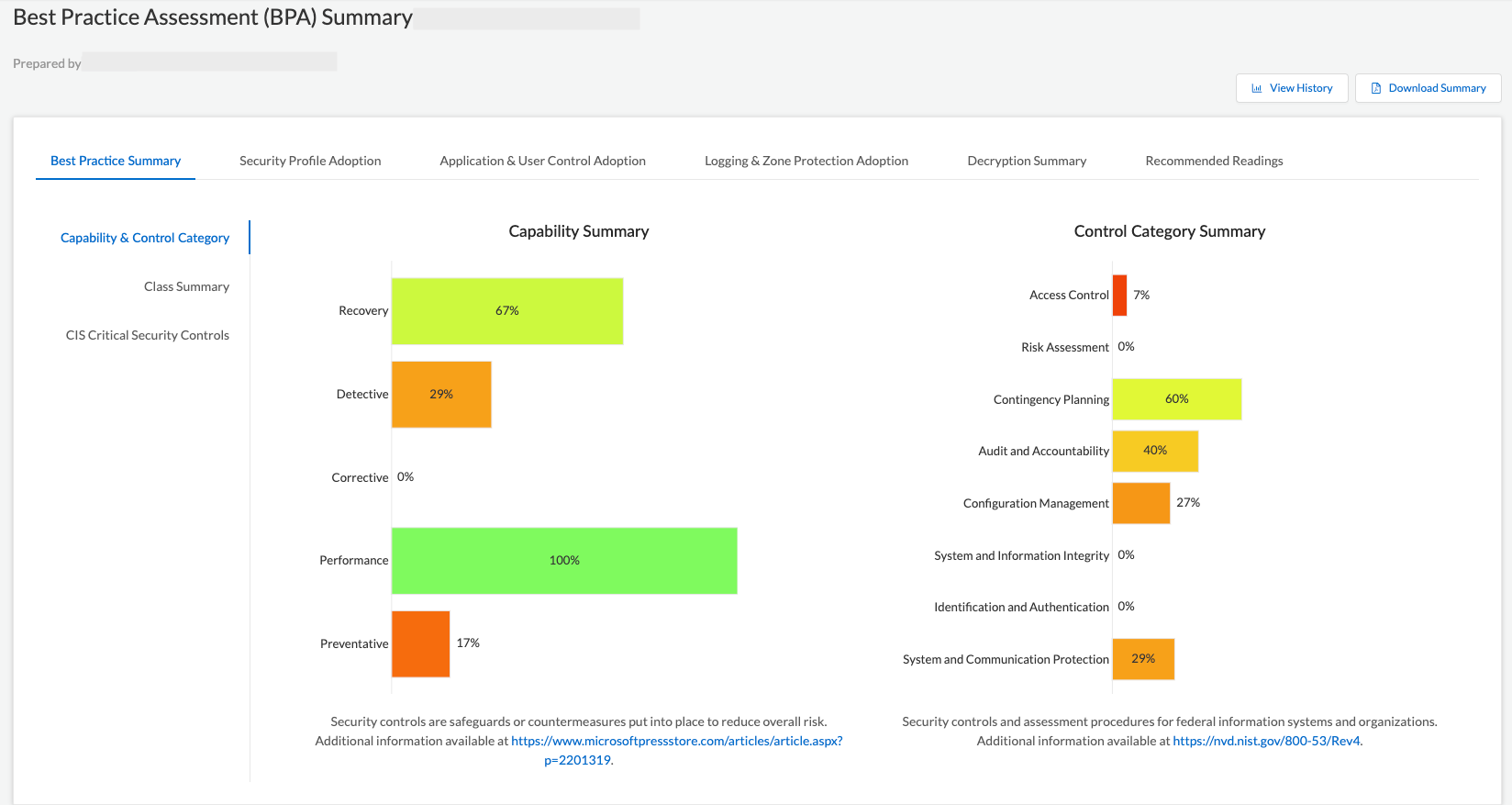
Immediately the website will present you with a summary of the BPA results.
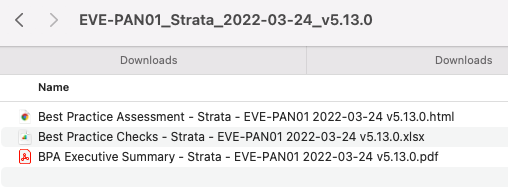
Once the zip file is extracted, you will see three files
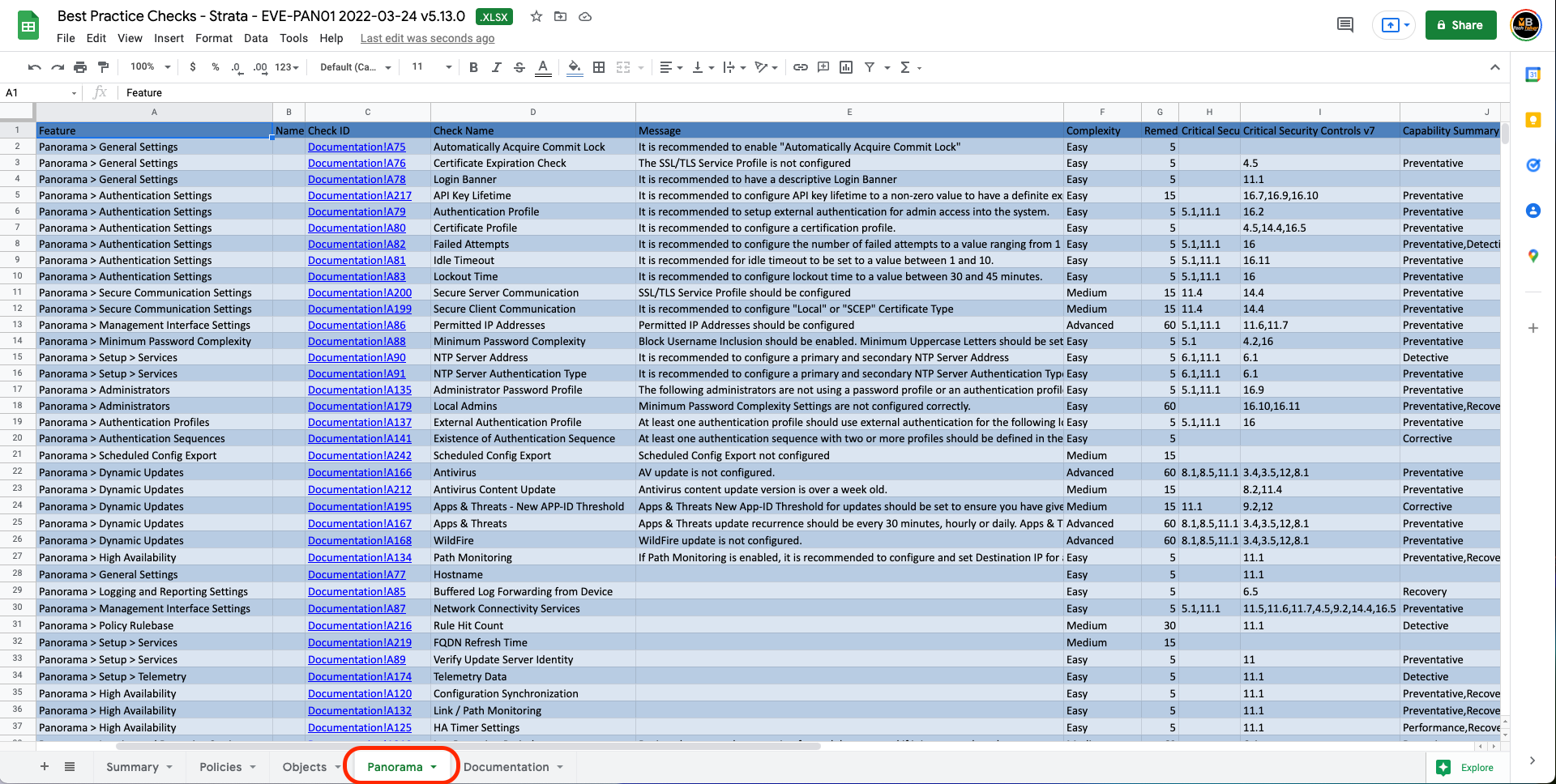
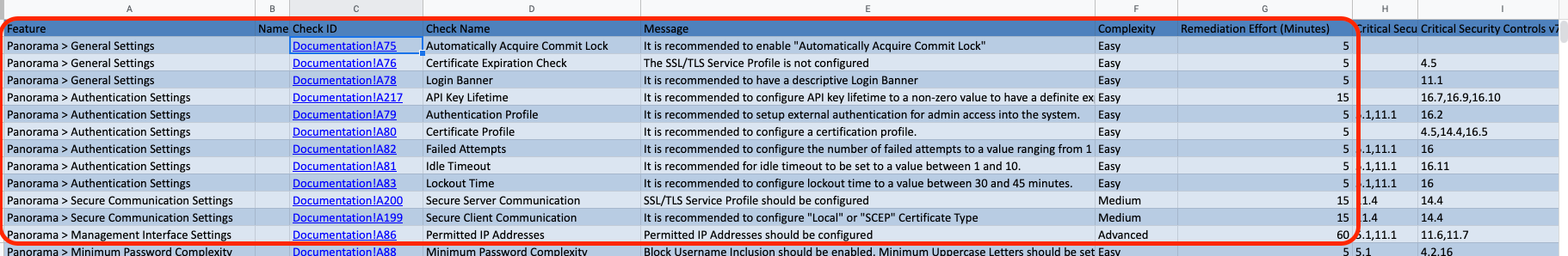
All BPA Executive summaries that are generated will be saved in Palo Alto Networks Customer Portal, and customers and partners will always have access to historic executive summaries, however, Palo Alto Networks does not save the detailed HTML reports, which is largely due to security and privacy concerns. Just remember to save the files for future reference! I'm not going to deep-dive into the detailed BPA report as the report focuses heavily on Strata Firewall best practices. I am solely interested in best practices for Panorama. Within the zip file, there is a .xlsx spreadsheet, and when opened, I will be working inside the Panorama tab
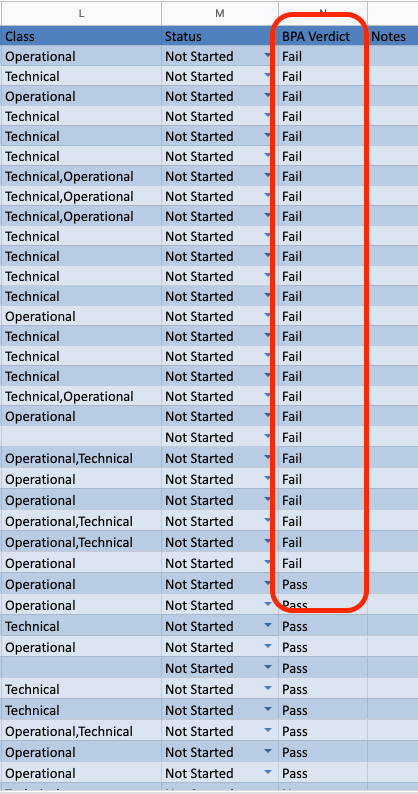
The BPA Verdict column shows a Pass or Fail status, this is where my work begins, I will go through each failed verdict, with the aim of running a BPA periodically to track the progress and improving the overall security posture of Panorama.
There is some really useful information in the spreadsheet that will guide me through each failed check, rating the complexity of the configuration change, the amount of time it should take me to configure that specific element and also provides me with hyperlinks to documentation and the rationale behind why the change should be remediated. Essentially this spreadsheet becomes a living document where all the remediations can be tracked.
I'm not going to through each BPA verdict in this article, however, you can check out my YouTube video where I demonstrate how I use this process, and go through some of the easy configuration tasks.