Panorama Baseline Configuration

Now that I have successfully deployed a Panorama KVM image in EVE-NG, I can now boot up the two Panorama virtual appliances and configure IP connectivity through the console so that each Panorama can be managed via the WebUI and SSH. The aim of this lab task is to have the two Panorama appliances configured in Active/Passive High-Availability mode, additionally configuring basic baseline configuration ready to manage Palo Alto Firewalls using templates and device groups.
With each of the Panorama nodes booted up, I can access them via the console directly in EVE-NG and configure the system hostname, IP address, default gateway, DNS server, timezone and NTP server.
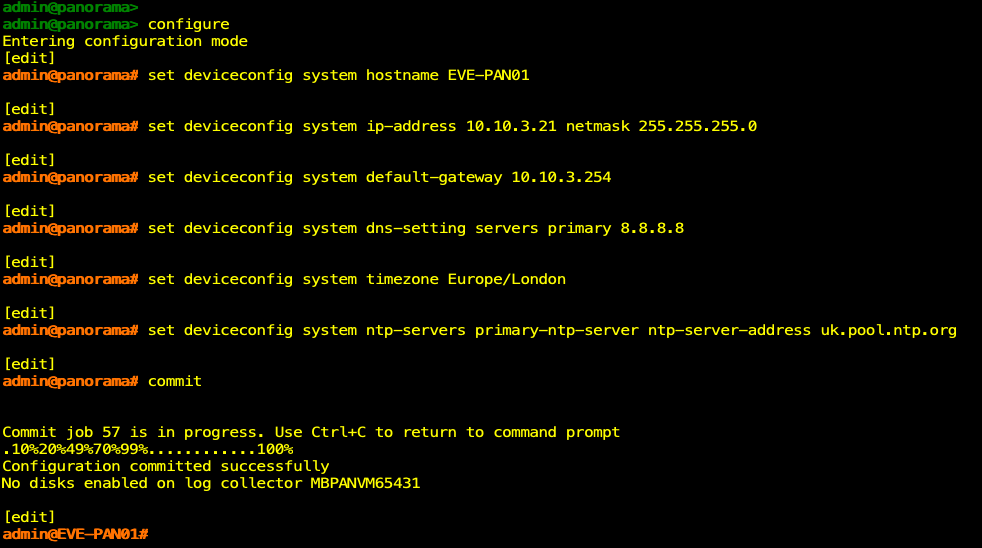
set deviceconfig system ip-address x.x.x.x netmask 255.255.255.0
set deviceconfig system default-gateway x.x.x.x
set deviceconfig system dns-setting servers primary 8.8.8.8
set deviceconfig system timezone Europe/London
set deviceconfig system ntp-servers primary-ntp-server ntp-server-address
Don't forget to commit your changes!
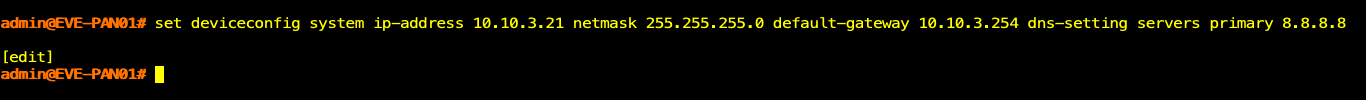
I didn't have to enter each command separately, for example, you could configure the IP address, default gateway and DNS servers in one command.
Set deviceconfig system ip-address 10.10.3.21 netmask 255.255.255.0 default-gateway 10.10.3.254 dns-setting servers primary 8.8.8.8
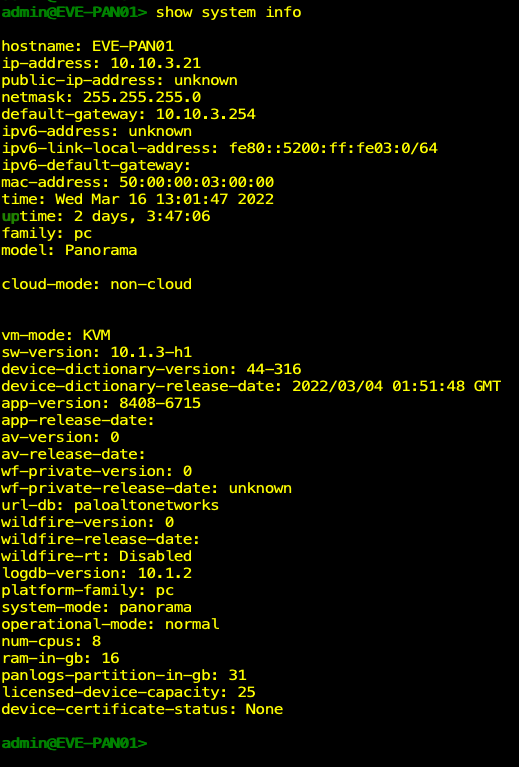
Once I committed the configuration, I issued the "Show system info"command to verify my settings were correct. I repeated the same steps on the second Panorama.
From the browser, I entered https://10.10.3.21, and was greeted with the Panorama login screen.

Once logged into both Panorama's, I retrieved the license keys from the server and was issued a Device Management License to manage up to 25 devices.
This was a good time to see if Panorama can reach the Dynamic updates servers over the internet, by navigating to the Panorama tab —> Dynamic Updates (on the left) This step was successful as the window populated with all the recent Anti-Virus, Applications and Threats and Wildfire updates, which I downloaded and installed.
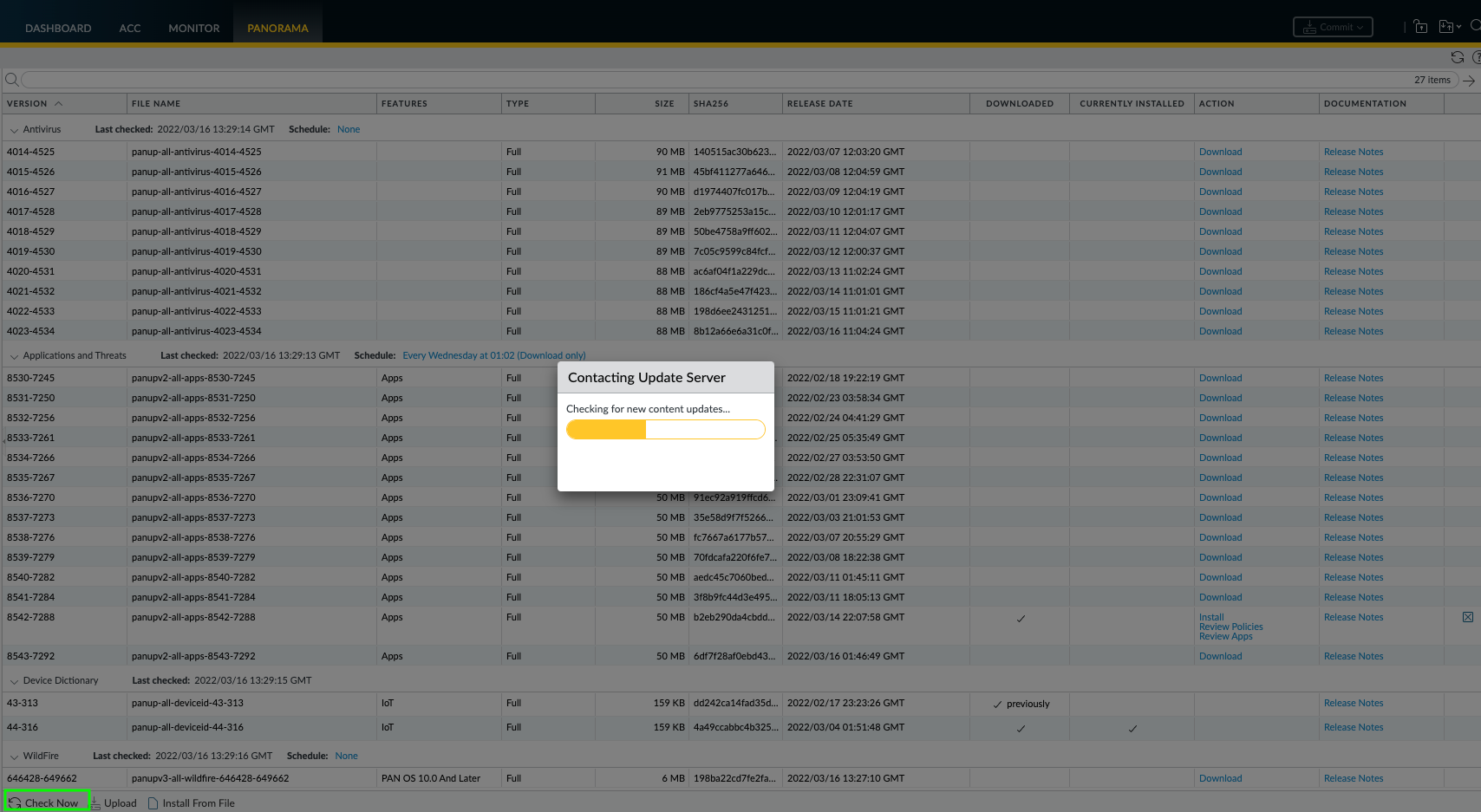
At this point, I had a basic configuration on both Panorama devices, at a later stage I will plan to run a Best Practices Assessment (BPA) in order to improve the security posture of the appliances.
My next step was to configure High-Availability so that there is an Active and Passive Panorama to provide redundancy. On EVE-PAN01 I navigated to the Panorama tab —>High Availability, In the Setup window, I enabled HA, provided EVE-PAN02's IP address and serial number. Then in the Election Settings, I change the Priority to primary and made sure preemptive was ticked so that if the Primary Panorama was to fail the Secondary would become Primary, however, if EVE-PAN01 was online again it would resume the Primary HA role. NOTE: If you are deploying High-Availability in a production environment please read through the Palo Alto Networks High-Availability TechDOCS to understand your requirements.
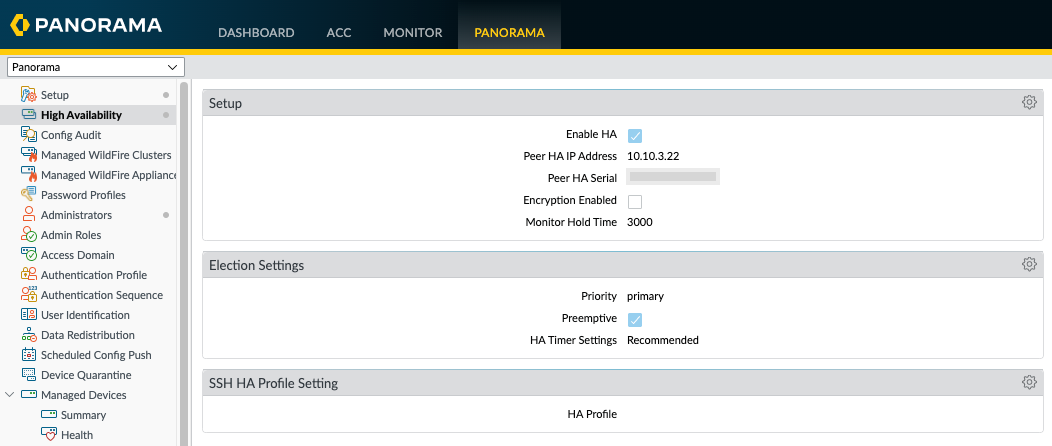
I double-checked my settings and committed the changes to Panorama.
And then repeated the steps on EVE-PAN02, but changed the IP address to the Primary -Active Panorama and changed the priority to secondary.
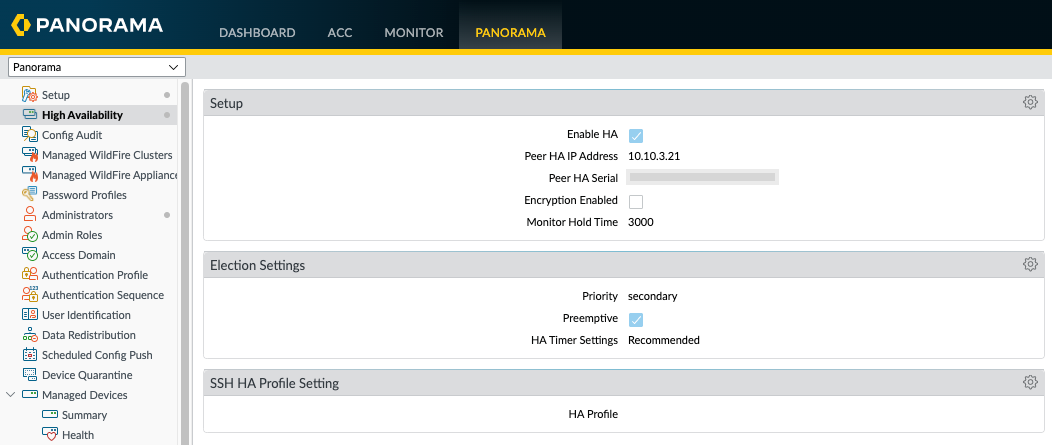
In order to view the High-Availability status, I needed to enable the High Availability widget in the dashboard on both Panoramas.
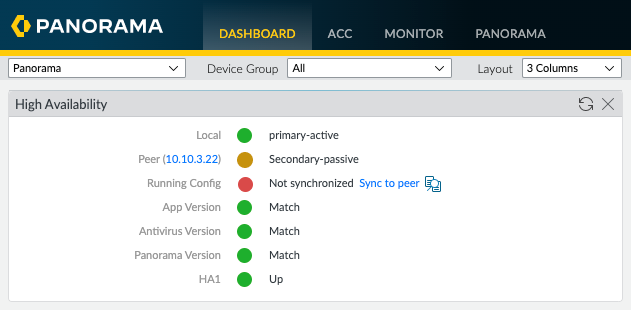
The widget provides a traffic light style indication of the High-Availability status. We can see that this local Panorama is the primary-active device and the passive peer is 10.10.3.22 (EVE-PAN02). The only issue I could see in red was the running configuration on this local Panorama is not synchronized with the Passive peer, so I went ahead and fixed that by clicking the "Sync to peer"
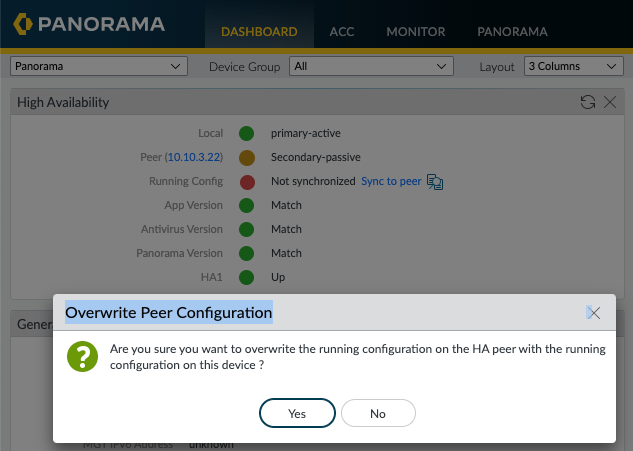
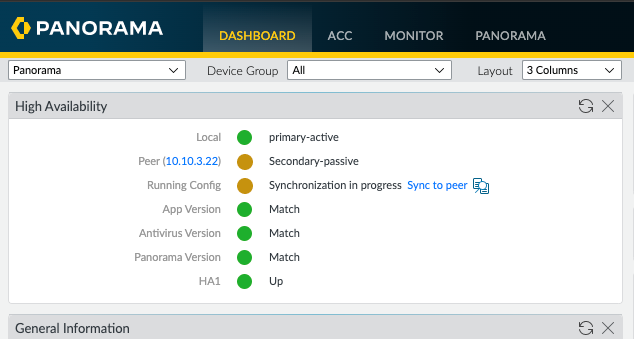
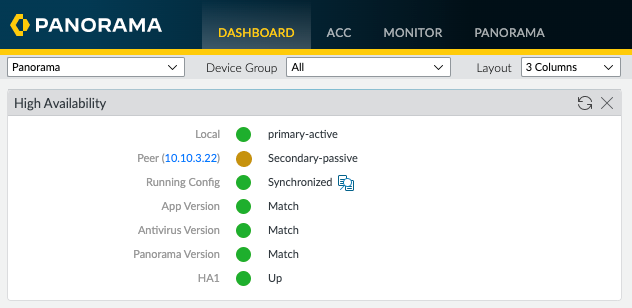
Now I have a synchronised Active/Passive pair of Panoramas with a basic baseline configuration. As I previously mentioned, I will run a Best Practices Assessment (BPA) against the Panorama configuration and start ticking off the failed elements of the BPA.