Migrate a HA Pair of PAN-OS firewalls into Panorama

When I deploy Panorama first time into the network, I always aim to have the least amount of local configuration on the firewalls as possible and allow Panorama to manage 99% of the configuration. However, in my lab, the firewalls do have some Security Policies and IPSec configuration which I will need to import into Panorama.
Up to this point, I have two virtual Panoramas deployed in an Active/Passive pair, I also have one pair of VM series firewalls also running in active/passive HA mode that is ready to be imported into Panorama. These are the steps I take to successfully get the firewalls under Panorama management.
In Panorama, I add the HA Firewalls serial number to Panorama and generate an auth key ready to paste into the firewalls Panorama management settings and commit to Panorama.
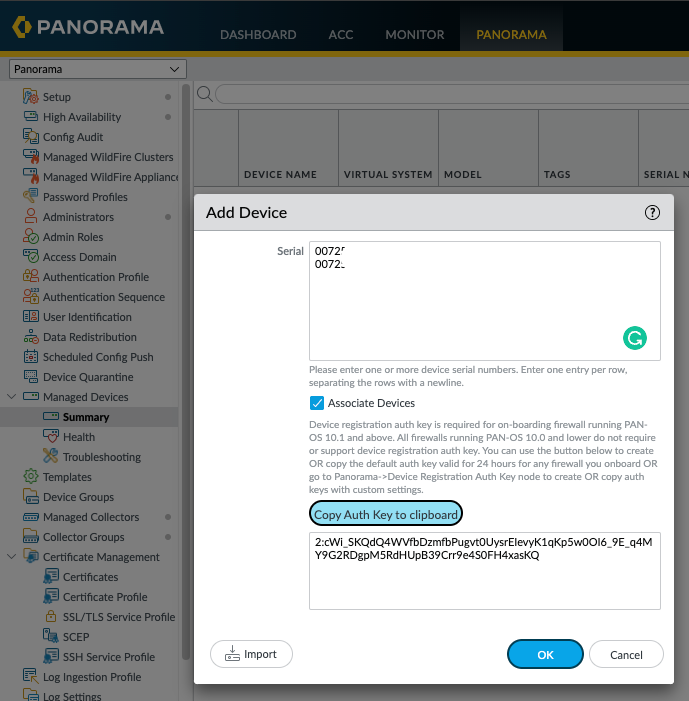
I Set the Panorama IP address on the Active firewall and paste the auth key into the box and click ok and commit. The Panorama IP will sync across to the passive firewall.
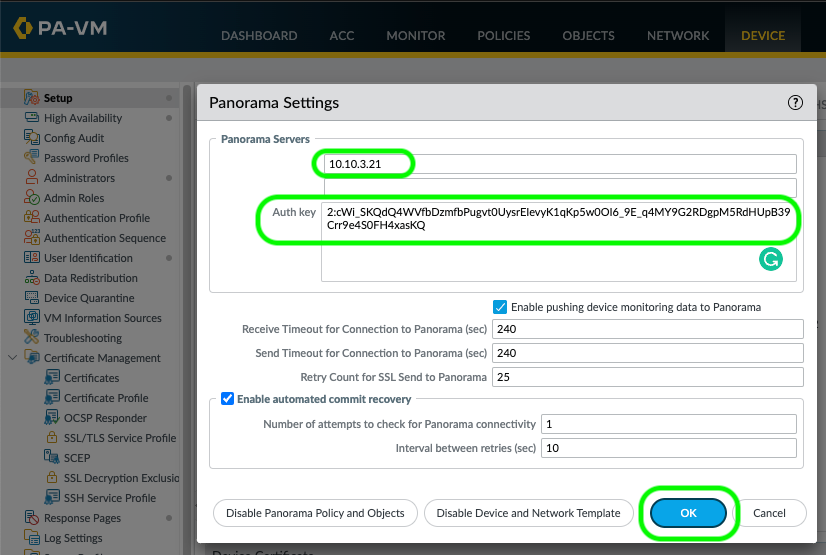
I noticed the auth key hadn't synced to the passive firewall, I pasted it in manually, I tried to commit and I got a message "No pending change to commit"
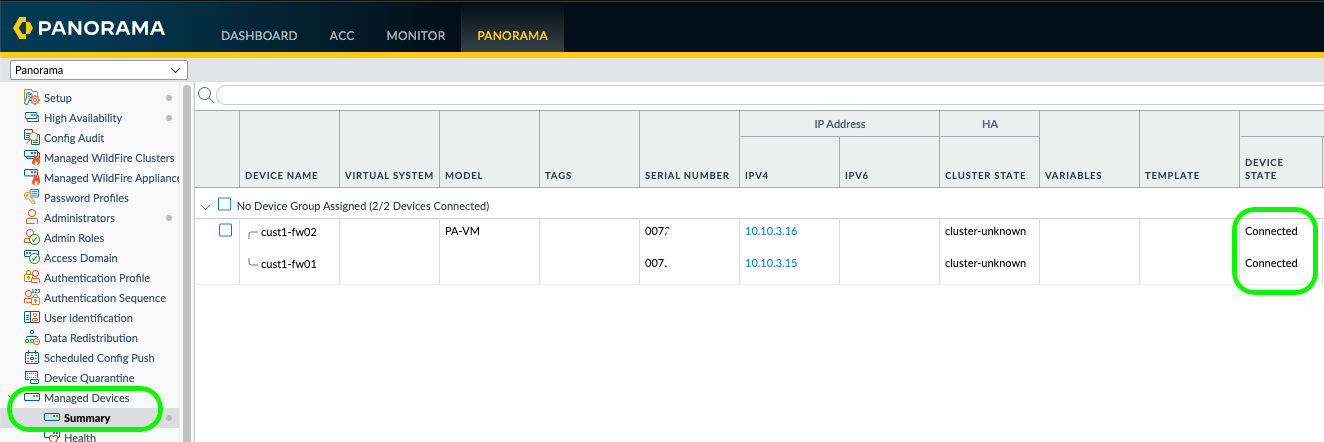
I checked to see if the firewalls were connected in Panorama, in the managed device summary, which they were. Looks like the auth key only needs to be added to one of the HA firewalls.
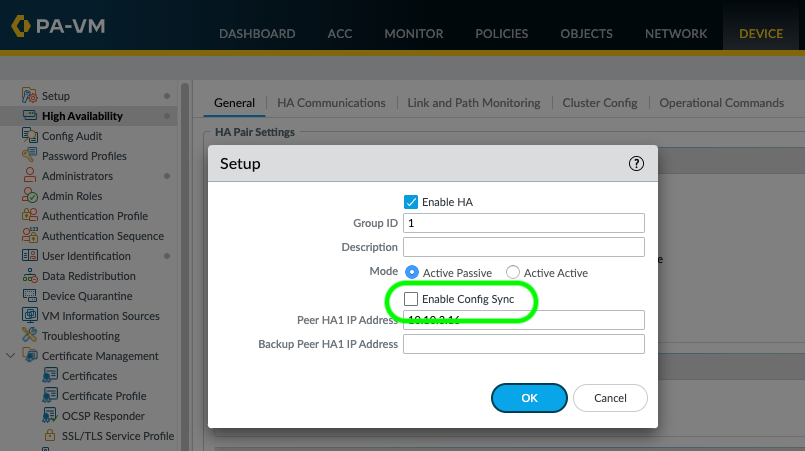
Next, I disabled config sync on each firewall, to ensure that the High Availability template configuration on the active firewall does not overwrite the Passive firewall HA configuration as the high-availability settings are unique. Then I did commit to both firewalls.
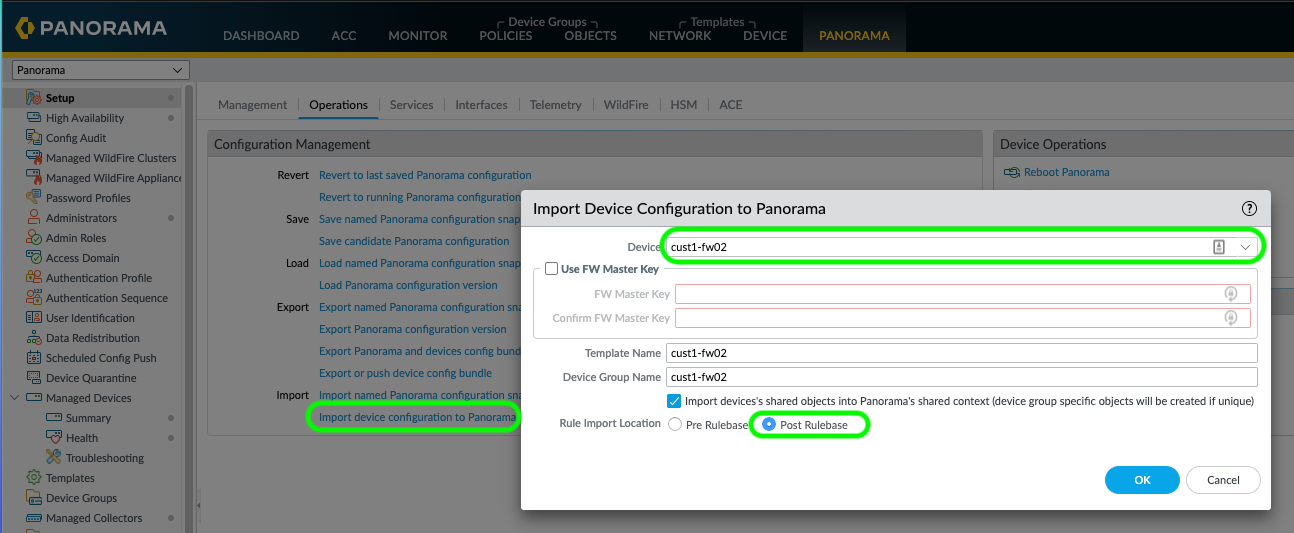
I then imported both of the firewall configurations into Panorama, I left the "Import devices' shared objects into Panorama's shared context (device group specific objects will be created if unique)" ticked, however, if I had a firewall with lots of objects I would untick this to avoid any duplication of objects, and I could always move the objects into the shared context at a later date. I put global rules in the Pre Rulebase such as blocking peer-to-peer traffic for all users or allowing DNS traffic for all users, In this case, I opted to import the firewall policies into the Pre Rulebase, as this is where I would define global deny rules, either by App-ID/services/user/IP based or a combination of both, or to create default zone to zone deny rules to use for logging of all blocked traffic.
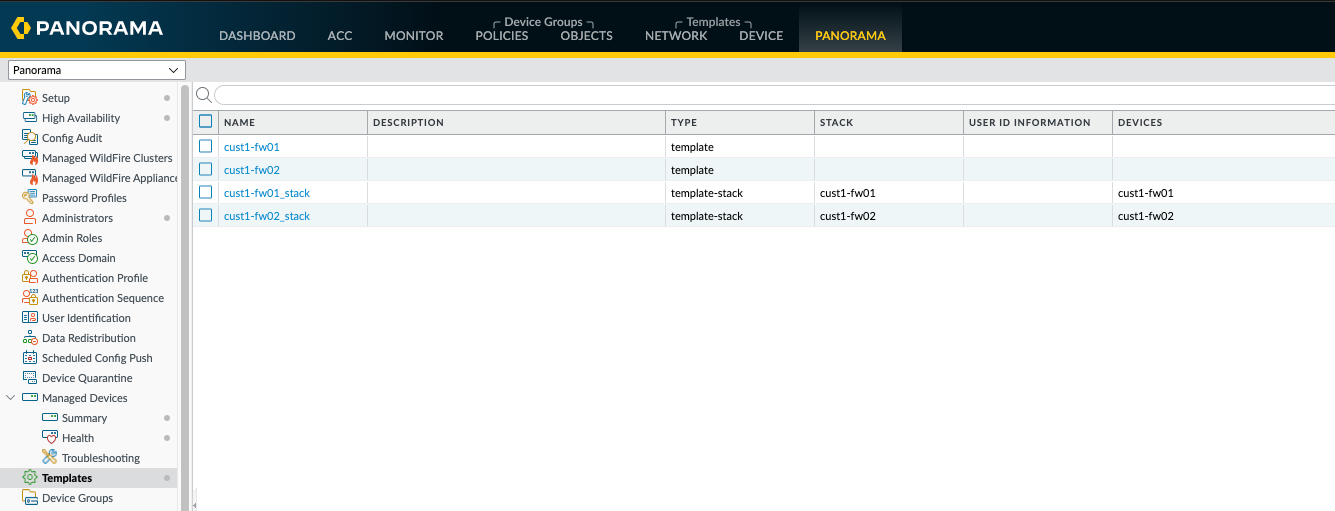
Now that both firewalls have been imported in, Panorama is now aware of the local configuration on the firewall.
Next, I cleaned up the templates. Both firewalls will be a member of one template Stack, so I renamed it to cust1-fw-01_o2_stack and deleted the cust1-fw02_stack and then moved the cust1-fw02 into the new cust1-fw-01_o2_stack.
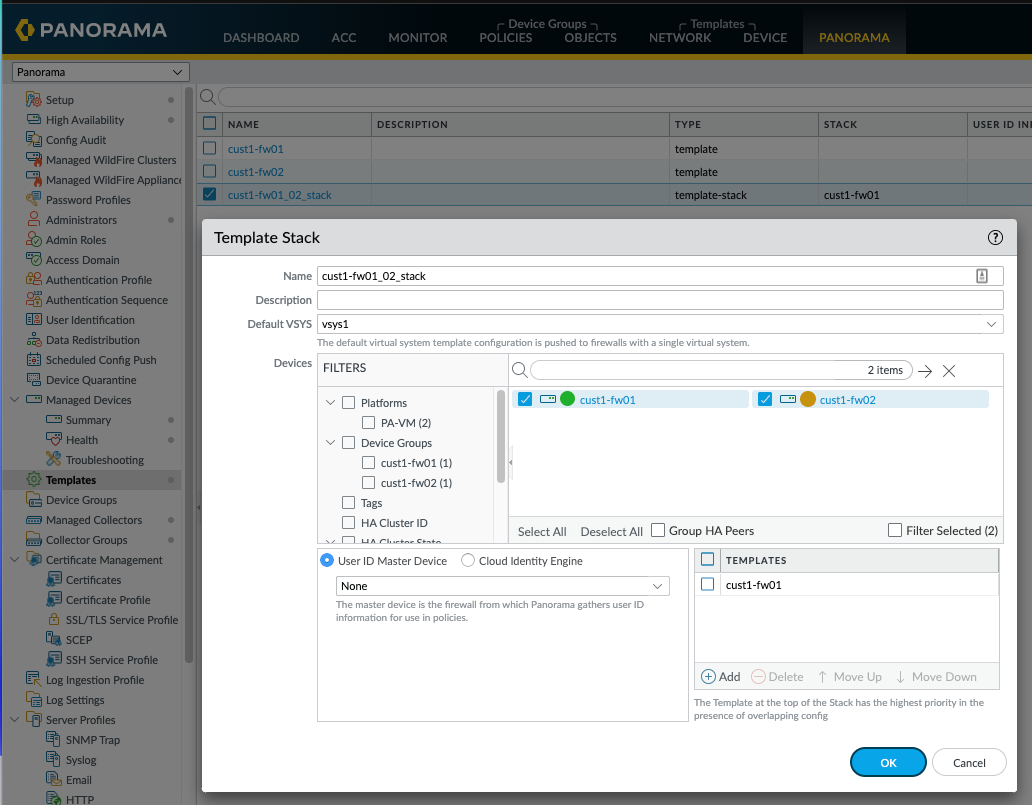
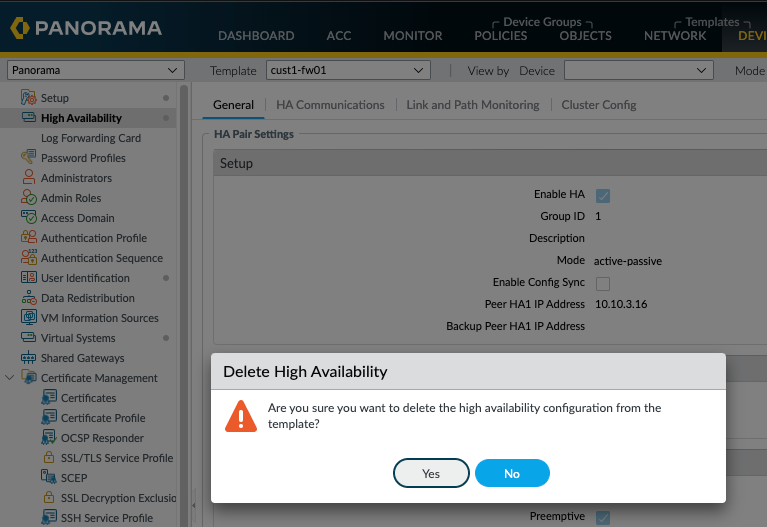
In my lab I've configured HA on the local firewalls themselves, I have no requirement for Panorama to manage these settings, So I removed HA config from each firewalls template within Panorama by clicking on the Device tab, High Availability and at the bottom click remove all. Commit to Panorama
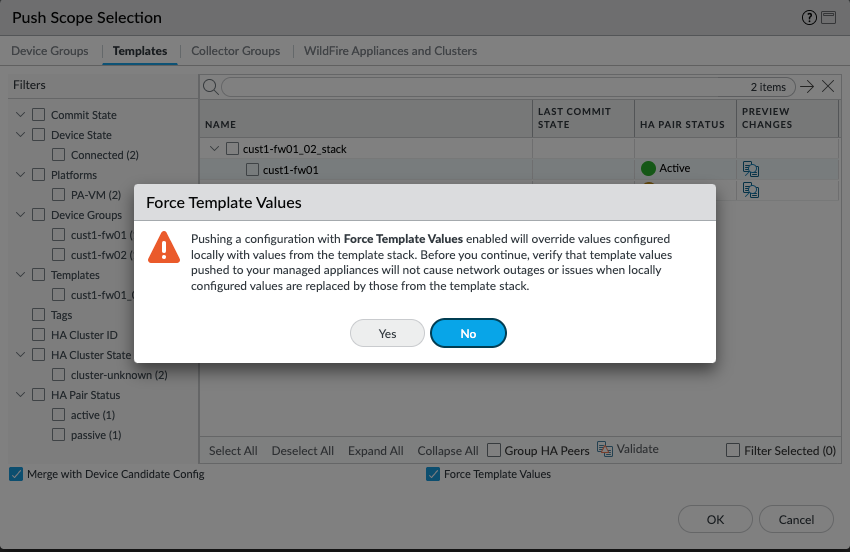
NOTE: A template configuration will not override the local firewall configuration unless you click "Force Template values in the Push Scope selection.
I then needed to export the device config bundle to both of the firewalls, this essentially replaces the firewall's local configuration with Panoramas managed configurations, the only local configuration in place will be the unique management settings like hostname, IP address, and High-availability settings.
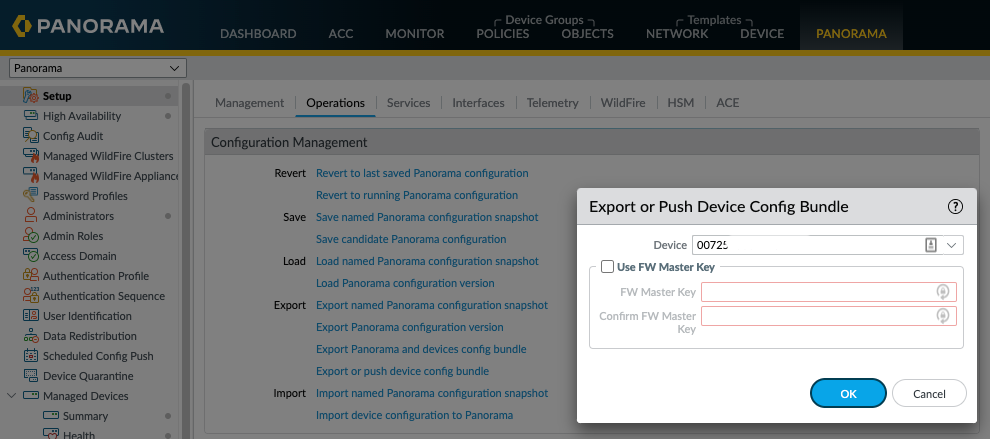
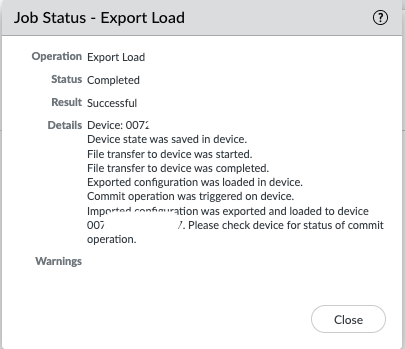
Once both device config bundle exports had been completed, I then performed a push to devices to both firewalls from Panorama.
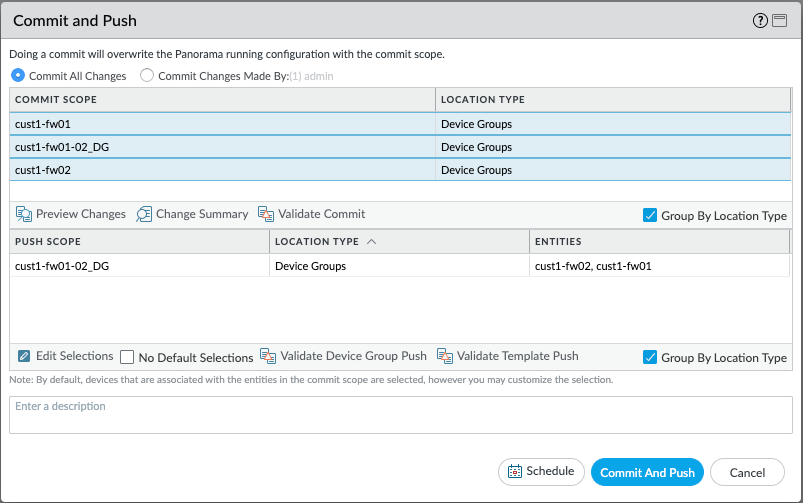
Now a little device group tidying up. I renamed the cust1-fw01 device group to cust1-fw01-02_DG, deleted the cust1-fw02 device group and then added cust1-fw02 to the cust1-fw01-02_DG. Now that both firewalls are a member of the cust1-fw01-02_DG, policies configured in this Panorama device group will get pushed to both of the firewalls.
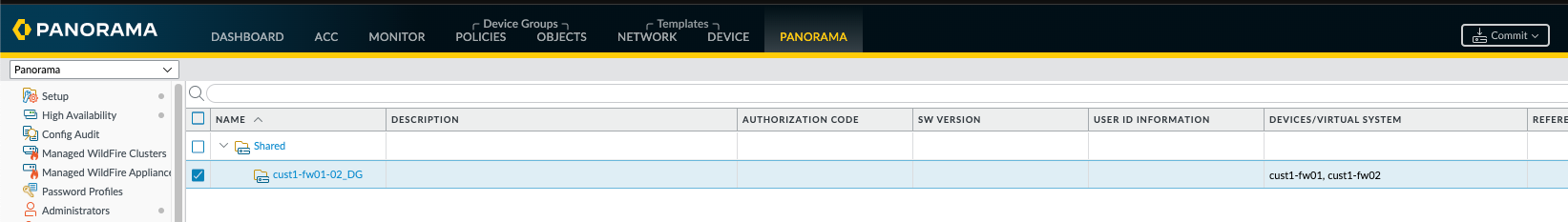
And then a final Commit and Push from Panorama
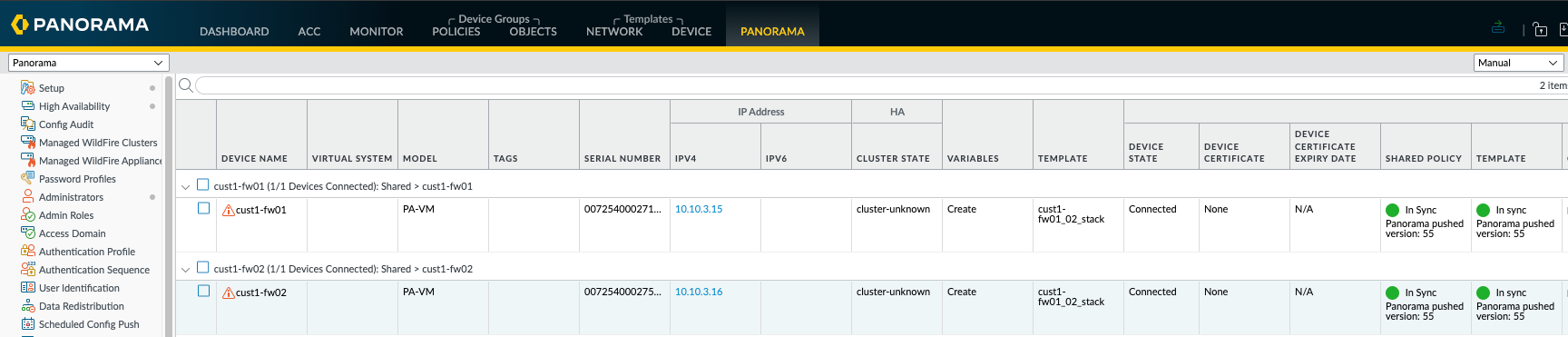
I checked in the managed device summary to check that the firewall policies and templated were in sync, I saw green icons that indicated everything was good!
The final step was to re-enable config sync locally on active/passive firewalls.
And that's it, I now have the ability to fully manage the HA pair of firewalls via Panorama.