How To Configure A Certificate For Secure PAN-OS Web-GUI Access

When using the WebUI to access a Palo Alto Networks firewall, you can use a certificate for all web-based management sessions, which will in turn get rid of those really annoying " Your connection is not private" warning pages.
If you are familiar with my YouTube channel you will know I use VMware Workstation to lab-up various Palo Alto Networks NGFW Configurations. In this post I explain how I configured a certificate for secure Web-GUI access to your Palo Alto Networks Firewall.
This process involved completing a new Certificate Signing request (CSR) on my lab Microsoft Active Directory Certificate Services Server, but first I had to generate a CSR from the PAN-OS firewall.
So from the device tab, I navigated to the Certificates section and clicked generate, I named the certificate "Webui-Firewall-Mgmt" In the Common Name field I used a FQDN which resolved to the firewalls management interface, which is WS-VM50-FW01-MGMT.mbtech.local which had a IP address of 192.168.21.21.
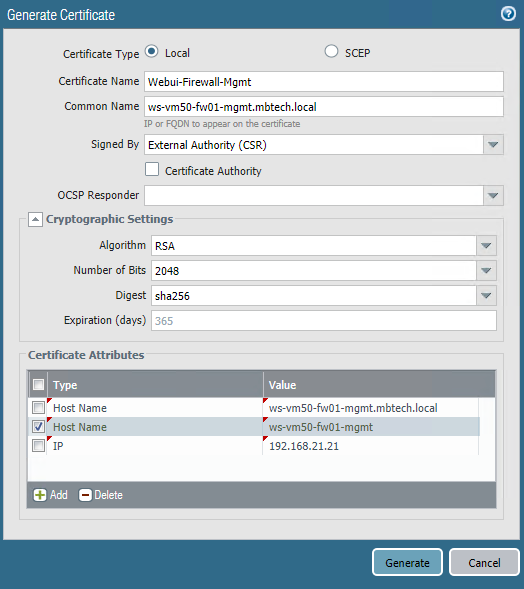
In the signed by field I selected "External Authority" which was my lab Certificate Services server. Instead of creating multiple certificates, I'm used the FQDN in the common name field and multiple Subject Alternative Names or SANs. This way I don't have to enter the long FQDN into the browser and can use the short hostname or the IP address. So in the Certificate Attributes section I added the firewall hostname and the IP address of the firewalls management interface and then when I was happy I clicked Generate.
Once the firewall had generated the certificate, I ticked the newly created cert and clicked "Export Certificate" on the bottom toolbar and then opened the CSR in Notepad I then copied all the text to the clipboard and made sure no spaces, browsed to the Microsoft Active Directory Certificate Services Web enrolment webpage at https://10.4.4.100/certsrv.
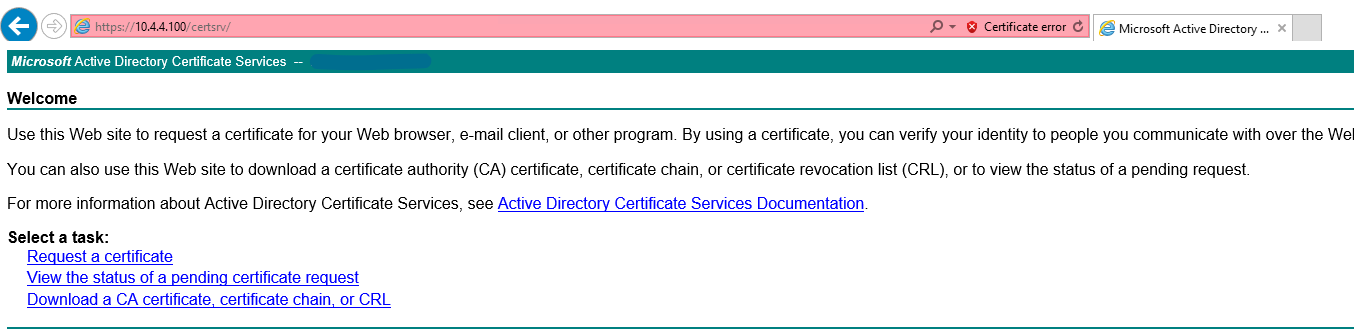
Under the "Select a task" section I clicked "Request a certificate" and then clicked "advanced certificate request"
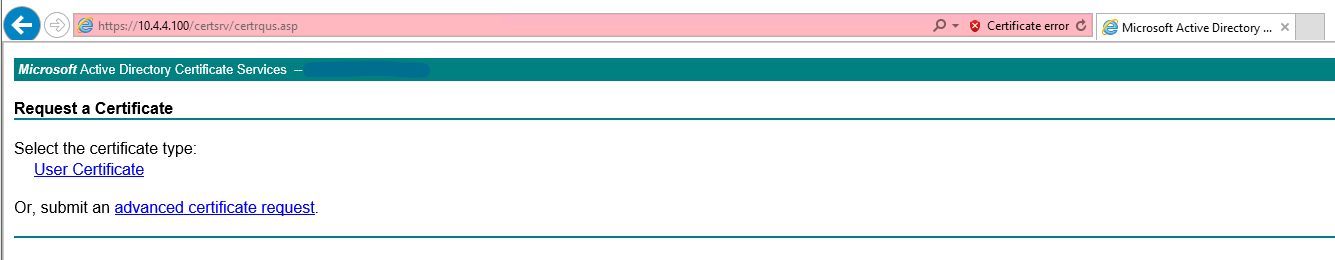
And then I clicked on "Submit a certificate request by using a base-64-encoded CMC or PKCS #10 file, or submit a renewal request by using a base-64-encoded PKCS #7 file"
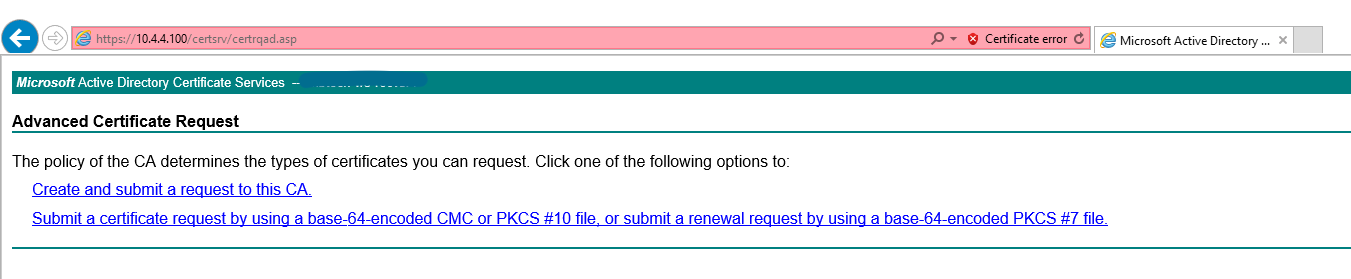
I then pasted the text from the notepad into the "Saved Request" box, changed the certificate template to "Subordinate Certification Authority" and clicked submit.
Once the certificate was issued, I downloaded as a Base 64 encoded certificate to the desktop and left it named as "certnew"

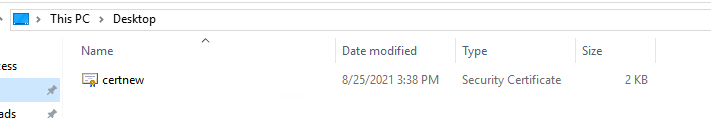
Back on the firewall, and still in the certificate section, I clicked and highlighted the pending certificate and clicked on import from the bottom toolbar, I needed to make sure I named the certificate name was identical to make sure the signing request matched, I then browsed to the "certnew" certificate and then clicked ok.
I saw that CSR was successful due to the status changed from "pending" to "Valid"

All that was left to do now was to create a SSL/TLS Service Profile so that certificate could be tethered to the firewalls management settings. I achieved this by navigating to the "SSL/TLS Service Profile" section, clicking add on the bottom toolbar and then give the profile a name and selecting the new signed certificate in the drop-down and clicking OK.
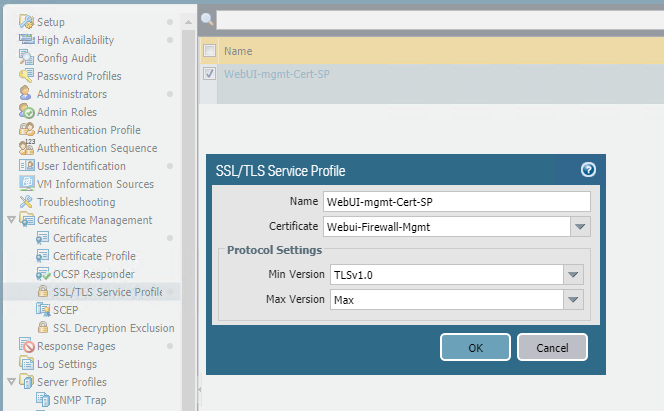
Still in the Device tab, I clicked on "Setup" and then the "Management" tab, and then the gear icon in the corner of the "General Settings" area, and in the SSL/TLS Service Profile drop-down I selected the Service Profile I created moments before and clicked OK.
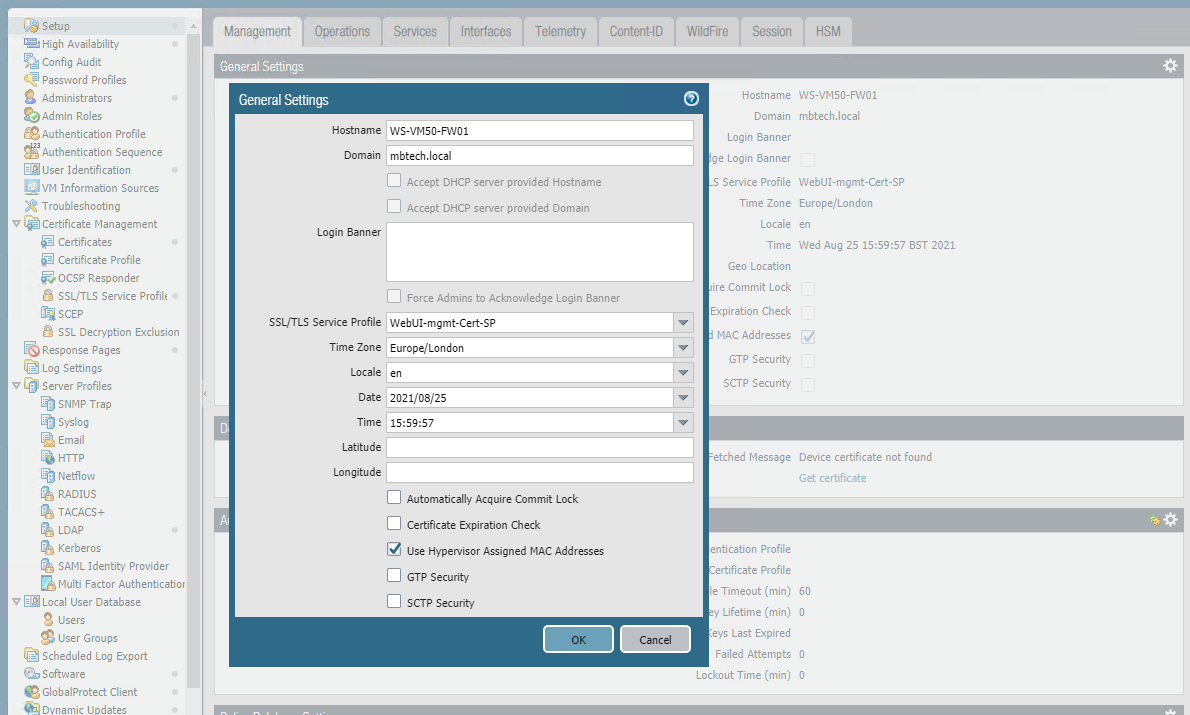
All that was left to do was hit the "commit" button and test.I noticed in the commit status window a message notifying me that the Web Server would be restarted and to refresh my browser.
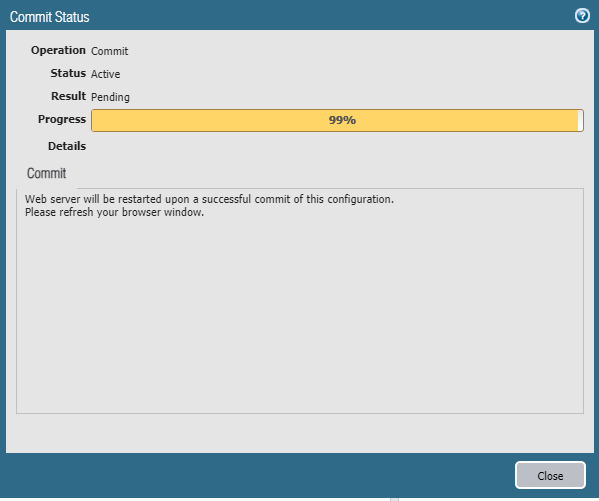
Once I refreshed my browser, I first logged in with the ip address, then the firewall hostname and finally the FQDN. Each connection was now trusted....no more annoying " Your connection is not private" warning pages yay!
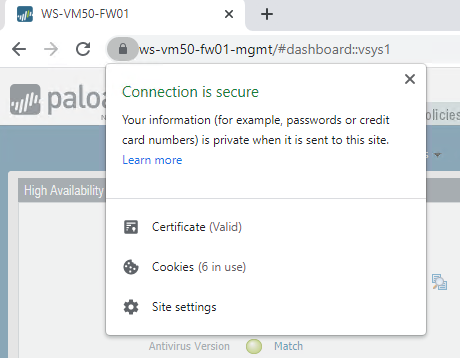
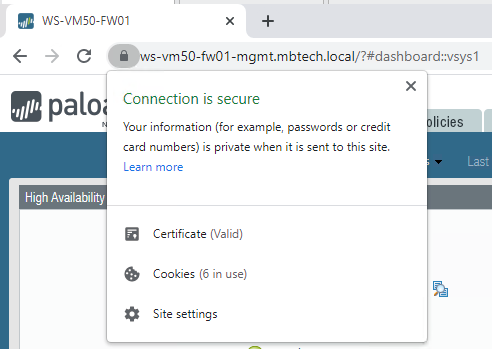
I just wanted to mention that I had a few issues with not seeing the "Subordinate Certification Authority" template in the drop down. I resolved this by running IE as an administrator and using HTTPS to access the Web Enrolment page.
Also be mindful if you are managing the firewall from a Virtual Machine machine that has to traverse the firewalls dataplane to reach the management interface and you are using SSL decryption you will most likely get decryption errors which can be seen in the traffic logs. What I did was create a security policy specifically for firewall management access and created a separate do not decrypt decryption policy that excludes the firewall management IP.


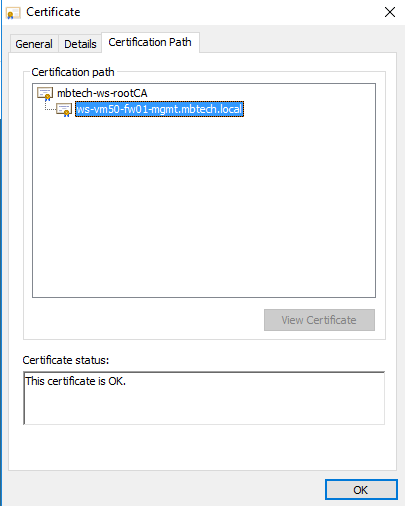
And don't forget that you will need the Root CA certificate in clients Trusted Root Certification Authorities cert store so that you browser can establish the chain of trust.
Check out this video on YouTube!